Android Forensics Tutorial – Part 1 Android Directory Structure
Android marketplace is growing multiple folds everyday, so the vulnerabilities, bugs and hacking activities associated with it. Today we will learn how to do Android Forensics tutorial from basics. This will be a series of tutorials. In this tutorial we will discuss Android directory structures. In later tutorials we will learn about android file systems, data acquisition, analysis, and various tools available for Android Data Extraction.
Android forensics is different from regular operating system or disk forensics because of various reasons. It supports multiple file systems which are specific to Android only. We may look for the following data on Android devices: SMS, MMS, emails, call logs, contacts, photos, calendars, notes, browser history, GPS locations, passwords, data stored on SD cards, etc.
So for extracting above mentioned data, it is important to understand file systems, directory structures, and how and where the data is stored on the devices before getting into actual forensics. So let’s start learning about Android Forensics…
Directory Structure of Android Operating System:
Android OS got its own directory structure which is specific to android only. We can look at android directory structure using “adb shell” or “DDMS” or something similar, there are lot of such small scripts in the market, you can easily find out using Google.
Note: Directory structure of Android can vary from device to device.
Below is sample directory structure of “SONY XPERIA E” device using “adb shell”:
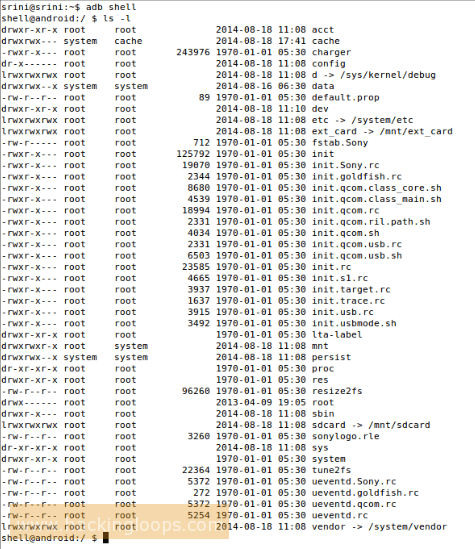
The above screenshot shows different files and folders on device. Now we want to know about data and folder which matters most for forensic analysts. Below are some most important places a forensic expert has to look upon:
- /system (system directory where operating system code exists)
- /data (it contains user specific data basically profile specific like data stored by SMS or MMS application, we can also see executable files of all applications at location “/data/app” directory but it requires root privileges i.e. a user without rooted device can’t see content of this directory. I have more for your guys. “/data/data/[app_package]/” directory is a place where user data for that application resides. But due to security reasons, data in each directory cannot be accessed by other applications. But there are multiple ways of doing that also which we will learn in later tutorials.)
- /sdcard (it is basically used for external storage where images, music files etc are stored but in our case (i.e. sony xperia) it stands for internal storage. So you need to debug more about /sdcard and /ext_card directories.)
Keep Learning !! Keep Connected!!
Do you need to increase your credit score?
ReplyDeleteDo you intend to upgrade your school grade?
Do you want to hack your cheating spouse Email, whatsapp, Facebook, instagram or any social network?
Do you need any information concerning any database.
Do you need to retrieve deleted files?
Do you need to clear your criminal records or DMV?
Do you want to remove any site or link from any blog?
you should contact this hacker, he is reliable and good at the hack jobs..
contact : cybergoldenhacker at gmail dot com